- What is a white label neobank platform?
- First, define the options in plain English
- The real comparison: what you get, what you trade, what you risk
- A founder-grade decision framework: 5 questions that matter more than features
- A practical “build vs white-label” scoring checklist
- The staged path most teams underestimate: white-label now, ownership later
- What to demand from a white-label platform before you commit
- What you must plan for if you go fully custom
- A practical next step with Finamp
Founders love the idea of “building a neobank,” but the real decision is more specific: do you build your own product from scratch, or launch on a white label neobank platform and brand it as yours?
That choice affects everything that matters in the first 6 to 18 months:
- how fast you can launch and validate demand
- how much capital you burn before you learn anything
- how much risk you carry in security, compliance, and uptime
- how flexible you can stay over the long run
That choice affects everything that matters in the first 6 to 18 months when choosing between custom builds, a white label banking app, or a Finamp white label neobank platform:
In practice, most successful teams do not treat this as a binary decision. They choose what to own (their differentiators) and what to borrow (infrastructure) using a build vs buy vs tailor approach.
This guide explains the trade-offs, gives you a decision framework, and shows a realistic migration path if you start with white-label but do not want to stay there forever. If you want a concrete delivery sequence, see our 30/90 approach here: How to Build a Neobank MVP in 2026 in 30 days and release in 90 days.
What is a white label neobank platform?
A white label neobank platform sits one layer above BaaS.
BaaS providers give you access to banking rails (and sometimes a banking core), but you still need to design and build the actual product: the apps, authentication flows, messaging, customer support tooling, operational workflows, fraud tooling integrations, analytics, and the day-to-day reliability work.
A white-label neobank solution like Finamp provides that missing product layer as maintained software:
- ready-made user experiences (a white label banking app and supporting components)
- pre-built integrations and workflows (auth, notifications, operational controls, typical fintech patterns)
- security and operational foundations that reduce the need for a large technical team early
- customisation capabilities so you can add your own logic, not just change colours
Most importantly, this model keeps you flexible long-term. If your BaaS partner changes, or you enter a market where your current BaaS is not available, a white label digital banking platform makes it easier to switch providers or add new rails (cross-border FX, crypto, fraud tooling) without rebuilding your entire product.
Finamp also supports code buyout for teams that later want full ownership: you can launch fast on a Finamp white label neobank platform, then purchase the codebase when you are ready to internalise development.
First, define the options in plain English
White-label (launch fast using an existing platform)
In this guide, “white-label” means a white label neobank platform that gives you a ready-to-run product layer (apps, admin, workflows, security patterns, and integrations) that you can brand and configure - without assembling everything from scratch.
This is different from pure BaaS: with BaaS you get banking rails and APIs, but you still build and operate most of the product yourself.
White-label is often paired with a sponsor bank or Banking-as-a-Service model, where regulated entities provide the underlying licensed components and connectivity, while you focus on product, distribution, and customer experience. (Tuum)
Custom (build your own stack)
Custom development means you build and operate your own application and services (mobile apps, backend systems, workflows, admin tools). You still might use partners for rails (card issuing, KYC vendors, payment processors), but the core product logic and system orchestration are yours.
Tailored build (the “middle path” most teams end up using)
The third path is “tailor”: you build differentiated layers on top of existing building blocks (cloud services, APIs, open-source, specialized vendors) rather than rebuilding everything from scratch.
The real comparison: what you get, what you trade, what you risk
Here is the quick mental model:
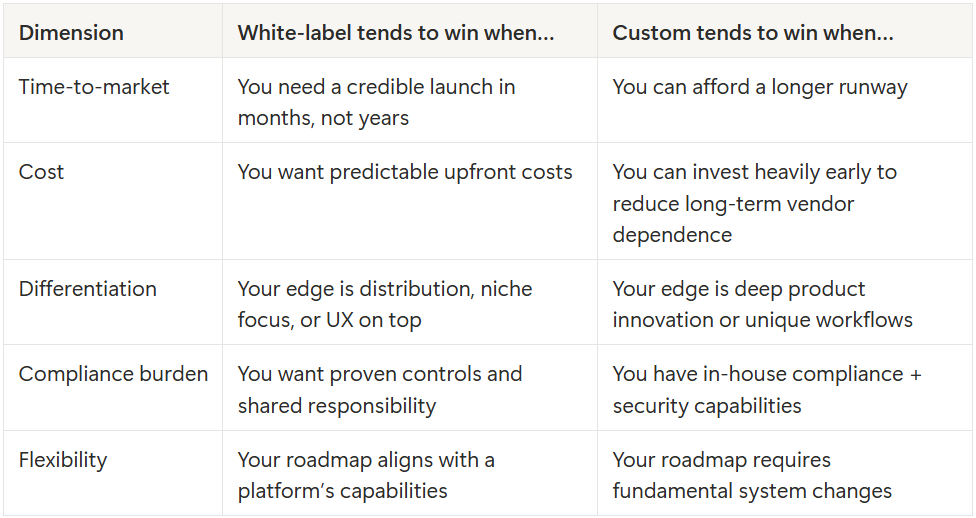
A founder-grade decision framework: 5 questions that matter more than features
1) How quickly do you need proof of market pull?
If your goal is to validate product-market fit, speed is an advantage. A white-label foundation can help you ship an MVP that feels bank-grade earlier, then iterate based on real user behavior.
If your goal is to build a new category with unique mechanics (for example, a novel credit underwriting model or complex enterprise workflows), custom might be necessary sooner.
A practical benchmark: most early-stage teams learn more from 90 days of real usage than from 9 months of internal planning. White-label and tailored builds exist to shorten that learning loop.
2) What do you need to differentiate on in year one?
Many founders underestimate how many “bank basics” must work reliably before users care about your unique idea.
If your differentiation is:
- a narrow segment (students, gig workers, SMEs in one niche)
- distribution partnerships
- a superior onboarding and support experience
- a feature sequence that drives retention
…then white-label or tailored build often makes sense, because you can spend energy on what users actually feel.
If your differentiation is:
- novel ledger behavior
- unique pricing logic tightly coupled to the core account model
- real-time risk decisions across multiple products
- deep integrations into client workflows
…custom becomes more attractive, because you will eventually fight platform constraints.
3) How much compliance and security responsibility can you carry?
This is where many build vs white-label debates become real.
A neobank app touches sensitive data, money movement, and identity. Even if you use partners, you still need a security posture that survives partner due diligence and customer trust.
Examples of what “bank-grade” often implies:
- Card data handling: if you store, process, or transmit cardholder data, PCI DSS applies, with defined requirements and assessment expectations. (PCI Security Standards Council)
- Mobile app security: OWASP MASVS is widely used as a baseline standard for mobile application security verification. (OWASP Mobile Application Security)
- Identity and authentication: NIST’s digital identity guidelines (now updated in the 800-63-4 revision) outline risk-based approaches for identity proofing and authentication. (pages.nist.gov)
- Information security management: ISO/IEC 27001 is a recognized standard for building an ISMS, often requested in enterprise partner reviews. (iso.org)
- Independent assurance: SOC 2 reporting provides assurance on controls across security and related trust criteria. (aicpa-cima.com)
White-label can reduce the “reinvent everything” problem by inheriting proven controls, but it does not eliminate your responsibility. You still own your policies, your incident response readiness, your customer communications, and your specific implementation choices.
Custom development gives you more control, but also means you must build and maintain more of the security and compliance machine yourself.
4) What is your true total cost of ownership?
It is tempting to compare:
- white-label subscription fees vs
- custom development project cost
That is not a fair comparison. The real TCO includes:
- engineering build cost
- ongoing maintenance and refactoring
- compliance audits and security testing
- on-call operations, monitoring, incident response
- partner integration upgrades
- app store releases and support load
Even “simple” banking apps often fall into a wide cost range depending on scope and compliance depth, and vendor estimates can span from tens of thousands for basic MVPs to hundreds of thousands or more for production-grade builds. (Leanware)
A more useful framing is this:
- White-label shifts cost from upfront build to ongoing platform spend, often reducing early burn but increasing dependence.
- Custom front-loads cost and risk, with the potential to reduce vendor dependence later, but only if you have the team to maintain it.
5) How much platform constraint can you tolerate?
White-label is fastest when you accept the platform’s defaults. Problems appear when your roadmap starts diverging.
Before choosing a white-label vendor, be clear on what you must control:
- Can you own your UX fully, or only theme it?
- Can you add new workflows (SME approvals, special fee models), or are you limited to configuration?
- Do you have data portability and export options?
- Can you integrate your own analytics, experimentation, and feature flags?
- What happens if you want to migrate off in 18 months?
If you cannot answer those, you do not have a platform. You have a dependency.
A practical “build vs white-label” scoring checklist
Use this quick scoring approach. For each statement, mark Yes or No:
You should lean white-label (or tailored build) if:
- You need to launch in under 6 months.
- Your early edge is distribution or niche positioning.
- You do not have a senior security + compliance bench in-house.
- You want predictable early cost and lower operational overhead.
- You are willing to ship with a smaller set of products first.
You should lean custom if:
- Your differentiation requires changing core money behavior or ledger logic.
- You need unusual workflows that a platform cannot support.
- Your partners require deep control over hosting, data, or controls.
- You have strong in-house engineering leadership and operational maturity.
- You can fund a longer runway without relying on early revenue signals.
You should plan a hybrid if:
- You need speed now but want ownership later.
- Your roadmap includes multiple markets, products, or business models.
If you marked Yes on 11 or 12, you are a strong candidate for a staged approach: launch with a platform, then progressively own differentiating layers.
The staged path most teams underestimate: white-label now, ownership later
Here is a realistic migration path that avoids the “white-label trap”:
Stage 1: Launch on proven rails
Goal: validate demand, retention, and acquisition channels with bank-grade fundamentals.
What you should own:
- positioning, onboarding narrative, UX choices, support experience
- measurement (activation funnels, retention cohorts, drop-off points)
- customer feedback loop and roadmap prioritization
What you can borrow:
- core account infrastructure
- card issuing connectivity
- baseline compliance tooling
Stage 2: Add differentiating layers
Goal: make the product uniquely valuable without destabilizing the core.
Examples:
- smarter money movement UX and transparency
- niche budgeting, controls, and automation
- SME roles and approval flows
- personalization and segmentation
Stage 3: Own what differentiates and keep borrowing what doesn’t
Goal: reduce vendor constraints where they block strategy, not because “custom is cooler.”
This is where tailored build becomes powerful. You keep the building blocks that do not differentiate you, and you replace the ones that do.
This staged approach is also friendlier to fundraising: you can demonstrate traction early, then justify deeper investment into custom infrastructure based on evidence.
What to demand from a white-label platform before you commit
If you go white-label, you are choosing a long-term partner. Use a due diligence checklist that goes beyond “features.”
Architecture and extensibility
- API-first, modular components
- clear separation between configuration and custom development
- a roadmap process that you can align with
Security and compliance posture
- support for standards and controls that partners commonly ask about (for example, mobile security verification practices, ISMS alignment, third-party assurance)
- a clear PCI DSS approach if card data touches your environment
- strong audit logs and traceability
Data ownership and portability
- documented data export and migration support
- clear terms on data retention and access
- ability to instrument analytics and experimentation
Operations
- uptime history, incident response process, SLAs
- monitoring and alerting visibility
- support tooling for disputes, refunds, and customer issues
What you must plan for if you go fully custom
Custom is not “build an app.” It is “operate a regulated-grade system.”
At minimum, plan for:
- secure onboarding and identity orchestration (with risk-based authentication)
- mobile app security practices aligned with an industry standard baseline
- key management, secrets, and environment controls
- observability (logs, metrics, traces), plus on-call ownership
- admin tooling, audit trails, and operational workflows
- release management and app store compliance (the app stores have review rules that matter for financial apps, privacy, and security claims) (Apple Developer)
Custom can be the right move, but only when you are ready to run it as a long-term operation, not a one-off project.
A practical next step with Finamp
Finamp supports the “tailored build” approach that many fintech teams end up choosing: launch quickly on proven infrastructure, then progressively own the parts that differentiate your product. Finamp is also a white label neobank platform for teams that want to launch a real product fast, without assembling everything by hand.
That means you do not have to pick between “white-label forever” and “build everything from scratch.” You can scope a staged plan where:
- the MVP proves traction and trust with bank-grade fundamentals
- differentiation is built in layers (UX, workflows, segmentation, controls)
- the architecture stays flexible enough to support multiple markets and product lines without a rewrite
If you want a clear recommendation based on your stage, team, and roadmap, book a call and we will map a build vs white-label decision using a measurable framework (time-to-market, risk ownership, differentiation, and long-term TCO), then turn it into a realistic delivery sequence. This is the practical way to approach white-label vs custom neobank development without locking yourself into a single provider forever.


